Can malware bypass antivirus software?
What is malware?
The term "malware" refers to malicious software. This term encompasses many different types of malicious software such as viruses, trojans, worms, and ransomware, to name a few.
There are a number of these that are more aggressive and use sophisticated techniques to bypass security software such as antivirus or anti-malware that protect you. The reason we bring up is that many people feel safe not realising that this aggressive malware 'attack' will be undetectable by the antivirus. It will install itself in such a way that it turns off any triggers picked up by antivirus software. The antivirus will look at a new file or program downloaded from the internet, examining it in detail, and decides if 'this thing' is, in fact, a virus. An aggressive form of malware will change itself, so the set of instructions do not match what the antivirus is looking for, so will let it through.
After it is allowed on the computer, it will modify how the antivirus software works so that it can no longer stay up to date with the details of the latest malware. This change will mean that the now compromised antivirus software will tell the user that everything is fine when it runs a check. Therefore, bypassing the very mechanism set in place to help you.
The origin use of the term virus was due to the nature of how the malicious software would spread inside a computer, and it’s files and changes the files so it could carry on harvesting information, and replicating itself.
The nature of how malware and in particular ‘viruses’ spread and persisted leant itself well to using medical analogies and as such medical terms such as viruses and infection has been adopted. Much the same as in the human body, the virus doesn’t care; its sole purpose is to replicate, repeat, replicate.
If any of these symptoms below are visible on your system, please contact one of our cybersecurity professionals - you can never start too soon.

Do I have a virus/malware infection?
A few of the telltale indicators are: [1]
- Problems are shutting down or restarting your computer.
- Your computer feels slow - much slower than it used to be
- Some files are going missing
- Your system crashes often or there are a lot of new error messages.
- New pop-up windows - (keep an eye out for ones asking that you call a help center)!
- New installed applications (toolbars, etc.) that you don’t remember installing
- Overworked hard drive (the cooling fan or hard drive spin up when you aren't doing much)!!*
- Contacts are receiving emails from your account that you didn’t send.
- Your antivirus programs seem to be throwing up errors.
What is antivirus software?
Antivirus software, also known as "anti-malware" software detects (or tries to), prevents and removes malicious software on a device*. Antivirus and Anti-malware are essentially the same thing. The two terms are the same software product and try to serve the same purpose. The word "anti-malware" expresses that the software covers more than just viruses and can help with other ‘malicious software’ like trojans or ransomware.
If you are looking for a quality antivirus or anti-malware product, we recommend the one we use which is Malwarebytes for Small Business.
Why do cybercriminals use malware?
If you think about cybercriminals as a business, an illegal criminal one but also like legitimate ones they need to make profits and be efficient. Previously crime was done in person, this was a high risk low reward process. Criminals realised that crime online had little chance of arrest and could be scaled to millions of victims at the press of a few buttons.
One of the most efficient tools for this is malware.
One piece of malware such as ransomware or a banking Trojan can cost between $100-$500 and be sent out to millions of people.
Much like how our modern tech industry has made every product a service, so have Cybercriminals. Many types of Malware are offered as a service so the criminals do not need to build it themselves or even send it out. Below is a screenshot of FLUX ransomware-as-a-service (RAAS) [2]
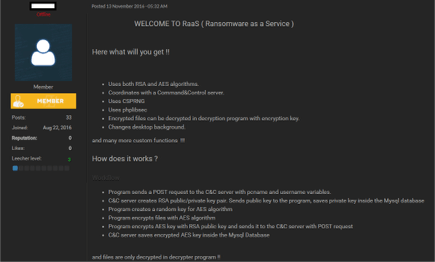
Online forums exist for criminals to sell criminals services or tools like malware. They use this not only to steal money out of your bank account but also information that like personal information (used for identity theft) or credit cards. Everything is to make a profit and they black market online.

How does malware work?
Many people wonder “How does malware get into your computer? - I don't remember downloading anything strange”
The ways that malware gets into your system are plentiful, but if we were to take a look at them all, there are two common ones - the internet (of course) and email. So if you are connected to the net (which you are - since you are reading this) then you are at risk.
Most infections come via infected websites, or emails and usually require an ‘installation’ of some kind - most of the time they require some form of permission to do this, but it is easy to be fooled by these official looking requests from trusted brands.
Criminals also use a missing security update which was used in automated worms like Notpetya or Wannacry.
Recently there has been a significant increase in attacks against mis-configured systems like the Windows Remote Desktop Protocol (RDP) which is a way to log into your computer from home and criminals guess your password or use information from stolen password or phishing sites to log into your computer and manually install the malware. This effectively bypasses many of the traditional cyber security such as antivirus but not the advanced network security monitoring.

How do I get malware?
Malware penetrates your computer when you click through hacked websites, install new toolbars from an untrusted developer, download infected music files or game demos, download free software that normally costs money. Quite often it is in an email from an unfamiliar provider when you open a malicious email attachment (called malspam). The biggest problem we face is that a system may have been infected for months before the user (you) realise. This is why having another independent check on your computer is valuable such as with network security monitoring.
Malicious apps like viruses and trojans can hide in seemingly legitimate applications, especially when they are downloaded from websites or messages and not from a secure app store.
When a new piece of software is installed, the warning messages presented by your operating system should tell you when unnecessary permissions are requested. Any software requested privileged access should be a concern, if you are unsure then please ask your IT administrator.
The first line of defence is making use of trusted sources, getting the software directly from the vendor, or the app stores. Never download or install apps from any other sites. There is a world of ‘bad actors’ out there, throwing tainted bait at you with an offer for some solution like an internet accelerator, a new faster download manager, or ironically a hard disk drive cleaner, or an alternative web search service.
That is, criminals take advantage of ‘a gullible version’ of you, someone willing to open up an email attachment you don’t recognize. Someone willing to click and install something from an untrustworthy source - don’t take this as “click-shaming,” because even very experienced people have been tricked into installing malware. (We have clients that employ entire teams to try and trick employees into installing software)
Even when you install something from a credible source, they may include in the permission request, additional unnecessary software. Secretly bundling extra software may end up with you installing some software you don’t want or need. This technique was a favoured way to get those annoying search bars installed in the past. This extra software, also known as a potentially unwanted program (PUP), is often presented as a ‘necessary component’, but it usually isn’t.
The most terrifying way to be infected is a blameless malware infection scenario. It is where a website has been hacked by a criminal and they have added malicious webpage. This webpage has a unique attack which takes advantage of a security flaw in common web browsers such as IE, Edge, Chrome, Firefox or Safari. This may be a webpage or even a banner ad will result in the unsuspecting victim having malware automatically installed. This is commonly referred to as a drive-by malware download.
Although it is not an intentional action from a user it is still due to a business not running an adequate cybersecurity program as checking for vulnerabilities in your computers, ensuring that they are automatically updating and monitoring for potential attacks can help prevent these attacks.
How does malware spread?
Every year the flu does its rounds, even though we may have had a shot last year, or have built up an immunity to previous year's version of the flu. The reason you can get sick every year is that the flu mutates all the time. Because it changes, our immune system doesn't recognize it as 'that pesky flu again', and it bypasses our immune system's defence.
These days we all live in cities, close to each other, continually touching and talking. We also find it very challenging to change our ways (Covid-19 is an example). The flu spreads quickly due to our society being very socially active and connected as a community. It is through our close interactions with other people that we can inadvertently spread it.
This cycle and spread are remarkably similar to how a computer virus or Malware spreads through its social connections and interactions. Think of our use of email, social media, websites as well as direct access to other computers over the internet. This social network allows it to hop from system to system, wherever the Malware finds a weakness in their protective system. Just like the flu, there is no predictable seasonality allowing us to anticipate the infections of computer systems or networks. Computer viruses and Malware are created by people which means they can happen at any time. The continuous creation of new Malware is a massive problem. Cybercriminals have found ways to make lots of money by creating millions of unique variations year on year.
You may have heard of the Wannacry or NotPetya outbreaks which were a form of Malware called Ransomware.
These impacted many organizations around the world and spread very rapidly. The reason they spread so fast is that they took advantage of a vulnerability in the Windows operating system that allowed them to gain unauthorized access to a computer automatically.
There are so many examples of different types of malicious software that take advantage of flaws in computer software. These range from attacks on the operating system like Windows or macOS, or a web browser like Chrome/IE/Edge/Safari. Others make use problems in Microsoft's Office suite like Word, Excel or Powerpoint.
Many organizations forget to update their software and plugins, effectively leaving open the doors discovered by computer security experts. They rarely have programs or services that continuously monitor all their computers, phones and devices - leaving many insecure and out of date.
The review of current security updates and monitoring for attacks of these, however, is a core component of our Cyber Safety Service.
Why doesn’t antivirus work?
Now that you have a good understanding of Malware and how it works you may understand some of the challenges that antivirus has with detecting and removing it. We have spoken about this before in 5 reasons why antivirus fails to protect small business.
So, You've Got Malware. Now What?
If you realise that you have a malware infection
- Clean-up - Use a quality anti-malware product like Malwarebytes for Small Business.
- Put in controls to stop it happening again - like our Cyber Safety Service.
- Keep on top of computers security updates and insecure configurations - vulnerability testing (included in our Cyber Safety Service)
- Install endpoint solutions and ensure they are being update such as Malwarebytes for Small Business
- Monitor the network to look for the signs of malware spreading or communicating with known malicious computers
- Cyber Security Incident Response - have a plan (included in our Cyber Safety Service - Business plan)
- Have policies and procedures to drive good behaviour (included in our Cyber Safety Service - Business plan)
- Train your staff to make them aware of tricks that cybercriminals use to try and infect your business (included in our Cyber Safety Service - Business plan)
